Recently, changes are part of our everyday lives and we do not always keep up with them. After the entry into force of Regulation (EU) 2016/679 of the European Parliament and of the Council of 27 April 2016 on the protection of natural persons with regard to the processing of personal data and on the free movement of such data, and repealing Directive 95/46/EC (General Data Protection Regulation), switching to new versions of ISO standards 9001 and ISO 14001, the change and introduction of the new version of ISO / IEC 27005: 2018 – Information technology – Security techniques – Information security risk management – could stay unnoticed.
What changes has been introduced by ISO/IEC 27005:2018?
We have good news that the ISO / IEC 27005: 2018 standard does not introduce significant revolutionary changes in information security risk management. The structure of the standard still consists of 12 chapters and 4 annexes.
References to the latest version of ISO/IEC 27001, i.e. the international edition of 2013, were updated, because the previous edition of ISO 27005 was in 2011. It is worth noting that the guidelines contained in ISO/IEC 27005:2018 are not mandatory requirements. Also, the standard does not specify the risk assessment methods. Organizations are free to develop their own risk management approach based on the ISO 27005:2018 standard.
The main assumption of the ISO/IEC 27005 standard is the implementation of cyclical activities in information security risk management. The process approach is used for this purpose. It is pictured below.
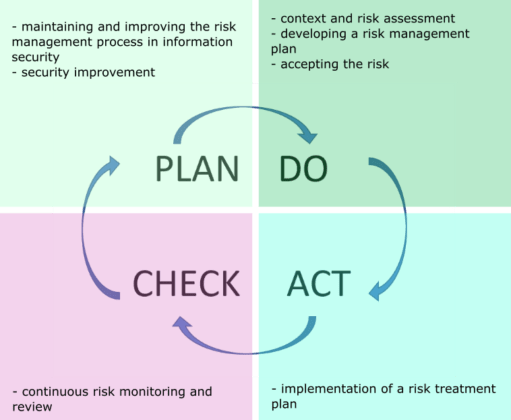

So we can translate risk management into specific actions:
- defining the context of risk management (scope, legal requirements, applied methods and approaches, risk preparedness and level of acceptable risk);
- analysis of relevant risk data and assessment of the organization’s information assets, security hazards, security gaps in order to determine the probability of an event, incident or its scenario and to determine the level of risk;
- impact on risk, taking into account risk levels and prioritization;
- stakeholders’ awareness about risk;
- continuous monitoring and reassessment of risk, as well as methods of impact on the risk, in order to identify significant changes and adequately respond to them.
It is the responsibility of each organization which declares compliance with the requirements of ISO/IEC 27001 to establish, implement and maintain a risk and opportunity management process in relation to the information security management system.
If you have questions about information security risk management, the need to implement ISO or other standards in the field of information and personal data security, don’t hstitate to contact our specialists!
We will conduct training in risk management in information security according to ISO/IEC 27005: 2018.

